In 2016, the Decentralized Autonomous Organization (DAO), a torchbearer in decentralized finance, was subjected to a crushing hack. The hacker managed to transfer over 50 million USD worth of digital assets by taking leverage of a vulnerability. The vulnerability is known as a Reentrancy attack, which shook the confidence of everyone connected to Blockchain technology.
Today, we dedicate this web blog to the Reentrancy attack in Smart Contract Code. Also, we will unmask the loopholes that pave the way for such attacks. So, stick with us till the end of this web blog to find out how developers and stakeholders can build a stronger and more secure future for Blockchain-based applications. Our previous web blogs on decentralized applications taught us about the importance of Smart Contracts.
Smart Contracts are a self-executing agreement that automates processes and eliminates intermediaries. When connected with cryptocurrencies like Ethereum, they show immense promise in finance & supply chain management. Smart Contracts ensure the predefined conditions are met before you complete a transaction. Let’s take an example of our marketplace. The smart contract would hold collectables in Escrow until the other party (buyer) confirms the payment. Even with the security, vulnerabilities like reentrancy attacks can manipulate the system to steal your digital attacks.
So why should you care about a Reentrancy attack? Reentrancy attacks in Smart contract codes can threaten the foundation of trust and security in a decentralized world. Understanding these weaknesses is important to safeguard the future of Apps and build a safe and reliable user environment.
Let’s understand the roots of what A Reentrancy attack in Smart contracts implies and why it matters.
What Is a Reentrancy Threat in A Smart Contract?
Reentrancy attacks in Smart Contracts harness a vulnerability within the Smart Contract code, allowing hackers to manipulate it. They enable an attacker to “Call Back” into a function’s execution to alter its result. Let’s take an example of a vending machine for your understanding. You insert a coin to get a drink, but the machine hands out the bottle before you pay. A Reentrancy attack, in a similar way, tricks smart contacts into releasing funds before the transaction completes.
Let’s break it down step by step.
1. The Deployment: A hacker or Attacker launches a transaction process with an unprotected smart contract code or function. Let’s say it’s a “withdraw” function to transfer assets from the contract to the user’s wallet.
2. Code Weakness: The Smart Contract first ensures the user has enough funds for the transaction before initiating the transfer. However, the code might not account for potential re-entries.
3. The Attacker Strikes: Before the transfer completes (funds haven’t actually left the contract), the Attacker calls the same “withdraw” function again from their own malicious code.
4. The Loophole Exploited: Unaware of the ongoing attack, the smart contract performs another balance check (which might still be valid) and attempts another transfer. This basically allows the hacker to come for round 2 to attack the user.
5. The user goes Broke: The hacker’s code re-enters the Smart contract function repeatedly until the balance is exhausted or reaches the limit (YIKES!).
Code Snippet Breakdown (Example in Solidity)
function withdraw(uint amount) public {
if (balances[msg.sender] >= amount) { // Check user balance
balances[msg.sender] -= amount; // Decrement user balance
payable(msg.sender).transfer(amount); // Transfer funds (vulnerable)
}
}
Popular Targets: Reentrancy attacks often target functions that involve:
A. Token Transfers
Functions that transfer tokens (cryptocurrencies) from the contract to a user’s wallet are prime targets.
B. Withdrawal Functions
Similar to token transfers, functions allowing users to withdraw funds from the contract are vulnerable.
C. Marketplace Transactions
On dApps facilitating buying and selling goods, functions handling payments or asset transfers can be exploited through reentrancy.
Reentrancy Attack Sequence Diagram
This diagram is a simplified Reentrancy attack on a vulnerable smart contract function.
A. Components
- Attacker Contract: A malicious contract designed to exploit the vulnerability.
- Victim Contract: The smart contract with the vulnerable function.
- User: The intended user interacting with the Victim Contract.
- Balance: Represents the user’s balance within the Victim Contract.
- Solidity Function Calls: Arrows represent function calls between contracts.
B. Steps
1. User initiates: The User sends a transaction to the Victim Contract’s `withdraw` function, requesting to withdraw a specific amount (denoted as `amount`).
2. Balance check: The Victim Contract checks the user’s balance to ensure sufficient funds.
3. Transfer initiated: If the balance is sufficient, the Victim Contract initiates a transfer of the `amount` to the user’s address (This step typically doesn’t complete the transfer immediately due to blockchain transaction processing).
4. Attacker Re-enters: The Attacker Contract triggers its own’ attack’ function upon detecting the `withdraw` function call.
5. Attack execution: The Attacker’s `attack` function exploits the vulnerability. It might:
Call the Victim Contract’s `withdraw` function again recursively, attempting to drain the user’s balance further.
Perform any malicious action enabled by the vulnerability, such as manipulating state variables or stealing funds from the Victim Contract.
6. State update (incomplete): After the initial transfer is initiated, the Victim Contract might update its internal state (e.g., decrease the user’s balance). However, this update might still need to be reflected on the Blockchain.
7. Attack benefits: Due to the re-entry, the Attacker might be able to exploit the temporary state inconsistency and gain unauthorized access to funds.
8. Incomplete transfer (optional): If the initial transfer from the Victim Contract to the user fails (e.g., due to insufficient gas), the user might not receive any funds despite the temporary balance decrease.
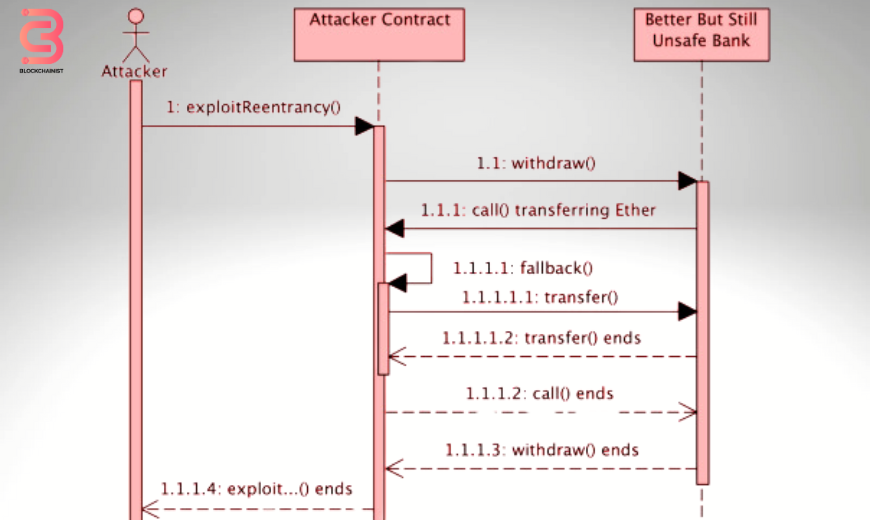
FIG: Sequence Diagram of a Cross-Function Reentrancy Exploit
Note for the readers: This is a simplified representation. The specific attack flow might vary depending on the vulnerability in the Victim Contract’s code.
Types of Reentrancy Attacks
There are different types of Reentrancy attacks, including:
1. Single Function Reentrancy: The most straightforward type, where the Attacker repeatedly calls the same vulnerable function within the target contract to drain funds or manipulate state variables.
2. Cross-Function Reentrancy: The Attacker exploits the interaction between multiple functions within the target contract.
3. Time-Stamp Reentrancy Attack: This is an attack in which an attacker manipulates the timestamp of a block. It causes a vulnerable contract to execute in favor of the hacker.
4. Cross-Contract Reentrancy: The Attacker leverages interactions between multiple contracts to execute the reentrancy attack.
5. Read-only Reentrancy Attack: An attacker might use a read-only function to gather information about the contract’s state. Later, the hacker uses that information to craft an attack.
How Can We Prevent a Reentrancy Attack on Smart Contracts?
Although reentrancy attacks are a major challenge, there are effective solutions to tackle this threat. Let’s break it down further;
- Prevention is Key
This attack includes operating on a read-only function to gather data about the contract’s state and use that information to attack. Building secure smart contracts starts with secure coding practices and design principles. Here are some key strategies:
i. Minimize External Calls
Limit the number of external calls (calls to other contracts) within a function, especially during critical operations like fund transfers.
ii. Check-Then-Effect Pattern
Implement a “check-then-effect” pattern. This involves verifying conditions (like user balance) before modifying the state of the contract (like transferring funds).
iii. Reentrant Flag
Consider using a Boolean flag to signal that a function is already in progress. This flag can be set at the beginning and reset at the end, preventing re-entry attempts.
- Safety Net of Solidity
High-level computer languages like Solidity have built-in features to eliminate or reduce reentrancy vulnerabilities. Applying the non-reentrant modifier to functions can prevent them from being called again & again when they are already in execution. These tools can be helpful if appropriately utilized within limits.
- Alternative Approaches
Beyond language-specific features, alternative coding patterns can achieve reentrancy prevention. Consider using libraries or frameworks that provide secure implementations of standard functionalities like token transfers. Additionally, exploring design patterns like the “Escrow Pattern” can offer secure transaction mechanisms.
- Code Review and Audits
Thorough code review processes are essential. Involving multiple developers with different perspectives can help identify potential vulnerabilities before deployment. Furthermore, professional, smart contract audits by security experts should be considered. These audits provide an in-depth analysis of code security and can uncover hidden vulnerabilities, including those related to reentrancy.
- Analyzing Past Mistakes
Real-world examples are daily reminders to realize the seriousness of the situation. Analyses of situations like the DAO hack in 2016 offer a roadmap for developers and security professionals. They can identify the previous hack pattern and build new and stronger defence mechanisms.
Wrapping Up!
Remember, folks! Reentrancy attacks are preventable if proper steps are taken and security tools are prioritized. Use the best available tools and best practices to create a future where dApps can be operated confidently. Let’s work together on this journey to be free from the fear of these digital exploits.
What Can We Do?
- Build Trustworthy dApps. Secure codes build trust in dApps, paving the way for wider adoption within the Blockchain space.
- The future of Smart Contracts security is bright. Advancements in security tools & growing awareness are building a more secure future for dApps.
- Developers can take proactive measures to secure Smart Contracts. They can utilize code reviews and audits to prevent reentrancy vulnerabilities. To stay informed, they can explore resources like security blogs and developer communities.
- Fortunately, developers are not alone in this fight. Security tools and libraries specifically designed to identify and prevent reentrancy vulnerabilities are readily available. Utilizing these resources can significantly streamline the secure coding process.
If you want to learn more about Smart Contracts and Blockchain Technology, check out our Blogs Section. Stay tuned to the Blockchainist for more educational and exciting content!
Let’s build a future free from reentrancy!